Findings Series: Weak Password Policy

Contents
Description
Applications and environments are often only as secure as their weakest user account password. To prevent initial compromise from occurring through account takeover, it is common to enforce complexity, length, and renewal requirements for passwords across an application or network. When these requirements are not stringent enough (or nonexistent) it is considerably easier for threat actors to achieve a foothold by leveraging common passwords.
If a Weak Password Policy is present, an attacker can attempt to compromise accounts through various techniques such as password spraying or credential stuffing. If they are successful, the attacker gains a foothold as a legitimate user, making them more difficult to detect unless user behavior is being monitored.
Classification
A weak password policy is a finding that is typically reported when the following conditions are not met:
- The domain or application allows users to set a password consisting of fewer than eight (8) characters.
- The domain or application allows users to set a password consisting of eight (8) characters but does not enforce any complexity requirements (uppercase, lowercase, number, special character)
Probability
Impact
High
Medium - High
Classification Criteria
Due to the ease of enumeration and exploitation, this finding is generally considered to have a high probability. The impact of a compromised account can vary depending on how well different types of accounts have been siloed, but a foothold is always considered to be at least medium severity. Should the attacker be able to escalate privileges beyond the initial account the impact rating will go up.
Examples
Domain Password Policy
Weak Password Policy can appear anywhere passwords are used for authentication. The actual weakness of the policy itself can be enumerated during account creation on the application, or within an Active Directory network using the Get-ADDefaultDomainPasswordPolicy PowerShell cmdlet:
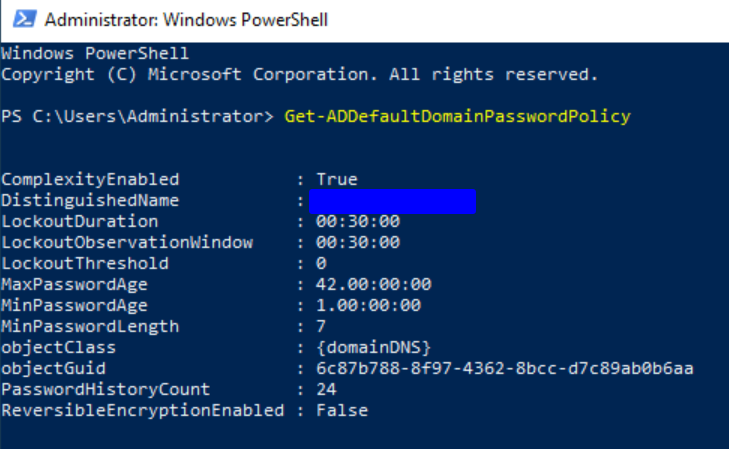
The above image includes the following information regarding the domain password policy:
ComplexityEnabled
- This specifies whether password complexity is enabled for the password policy. If enabled, the password must contain three of the following four character types:
- Uppercase characters (A, B, C, D, E, ...)
- Lowercase characters (a, b, c, d, e, ...)
- Numerals (0, 1, 2, 3, ...)
- Special characters (#, $, *, %, ...)
LockoutDuration
- This specifies the length of time that an account is locked after the number of failed login attempts exceeds the lockout threshold. The threshold is defined in the following format:
- D.H:M:S.F where:
- D = Days (0 to 10675199)
- H = Hours (0 to 23)
- M = Minutes (0 to 59)
- S = Seconds (0 to 59)
- F = Fractions of a second (0 to 9999999)
- D.H:M:S.F where:
LockoutObservationWindow
- This specifies the maximum time interval between two unsuccessful login attempts before the number of unsuccessful login attempts is reset to 0.
LockoutThreshold
- This specifies the number of unsuccessful login attempts that are permitted before an account is locked out.
MaxPasswordAge
- This specifies the maximum time interval that you can have the same password. The time interval uses the following format:
- D.H:M:S.F where:
- D = Days (0 to 10675199)
- H = Hours (0 to 23)
- M = Minutes (0 to 59)
- S = Seconds (0 to 59)
- F = Fractions of a second (0 to 9999999)
- D.H:M:S.F where:
MinPasswordAge
- This secifies the minimum time interval before you can change a password.The time interval uses the following format:
- D.H:M:S.F where:
- D = Days (0 to 10675199)
- H = Hours (0 to 23)
- M = Minutes (0 to 59)
- S = Seconds (0 to 59)
- F = Fractions of a second (0 to 9999999)
- D.H:M:S.F where:
MinPasswordLength
- This specifies the minimum number of characters that a password must contain.
PasswordHistoryCount
- This pecifies the number of previous passwords to save.
ReversibleEncryptionEnabled
- This specifies whether the directory must store passwords using reversible encryption.
Given the policy image posted, it would be classified as being weak due to the following criteria:
- The minimum password length is fewer than eight (8) characters.
- The lockout threshold is set to zero (0) indicating that the setting is disabled and therefore an account will not be locked out due to invalid authentication attempts.
Web Application Password Policy
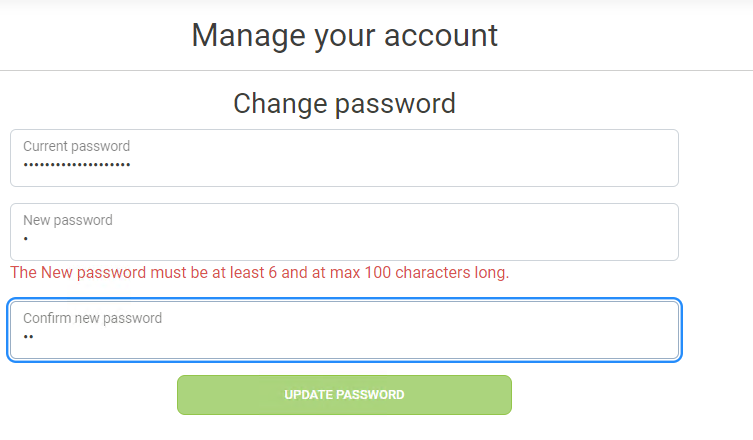
It is not uncommon for webapps to display the password requirements during account creation. Creating a dummy account for a web application allows attackers to enumerate the password policy of the application and can leverage this to guide wordlist creation for a password spray. If the password policy is weak then attackers will be able to significantly shorten their wordlist and still have reasonable probability of getting a hit. This makes it much easier to attack the vulnerable application and gain a foothold. The following shows the password change process for an application which includes a minimum length requirement of six (6) characters, which is unsufficient:
Remediation
Recommended password policy settings
Traditional password policy recommendations placed a large impact on the enforcement of password complexity to increase keyspace required for brute-force attempts. While true, this also results in users selecting predictable patterns to comply with the policy guidelines. If a policy requires an uppercase, lowercase, number, and special character, users will typically capitalize the first character of the password and tack on a single digit and special character at the end (e.g. Password1!). By enforcing regular changes, again users will fall into predictable patterns so that they can remember what they set their password to, resulting in extremely common occurrances of passwords such as Summer23!.
As a result, newer guidance recommends to extend or eliminate regular password updates and instead enforce a longer password length of twelve (12) or more characters without enforcing complexity requirements. This drives users to select something which is more difficult to guess and crack for an attacker, but easier for the user to remember due to the non-enforcement of the special characters. Therefore, for web applications, it's recommended to implement a similar policy of longer minimum requirements.
Updating Password Policy in Active Directory
Handling password policy will vary based on the underlying architecture and software used to maintain the network or web application. One of the more common ways is through Active Directory Group Policy. Many businesses use Microsoft Active Directory to manage their networks, workstations and users. From the Active Directory Group Policy Management Editor, create a new GPO and select Computer Configuration -> Policy -> Windows Settings -> Security Settings -> Account Policy -> Password Policy. You should see a GUI similar to the one below:
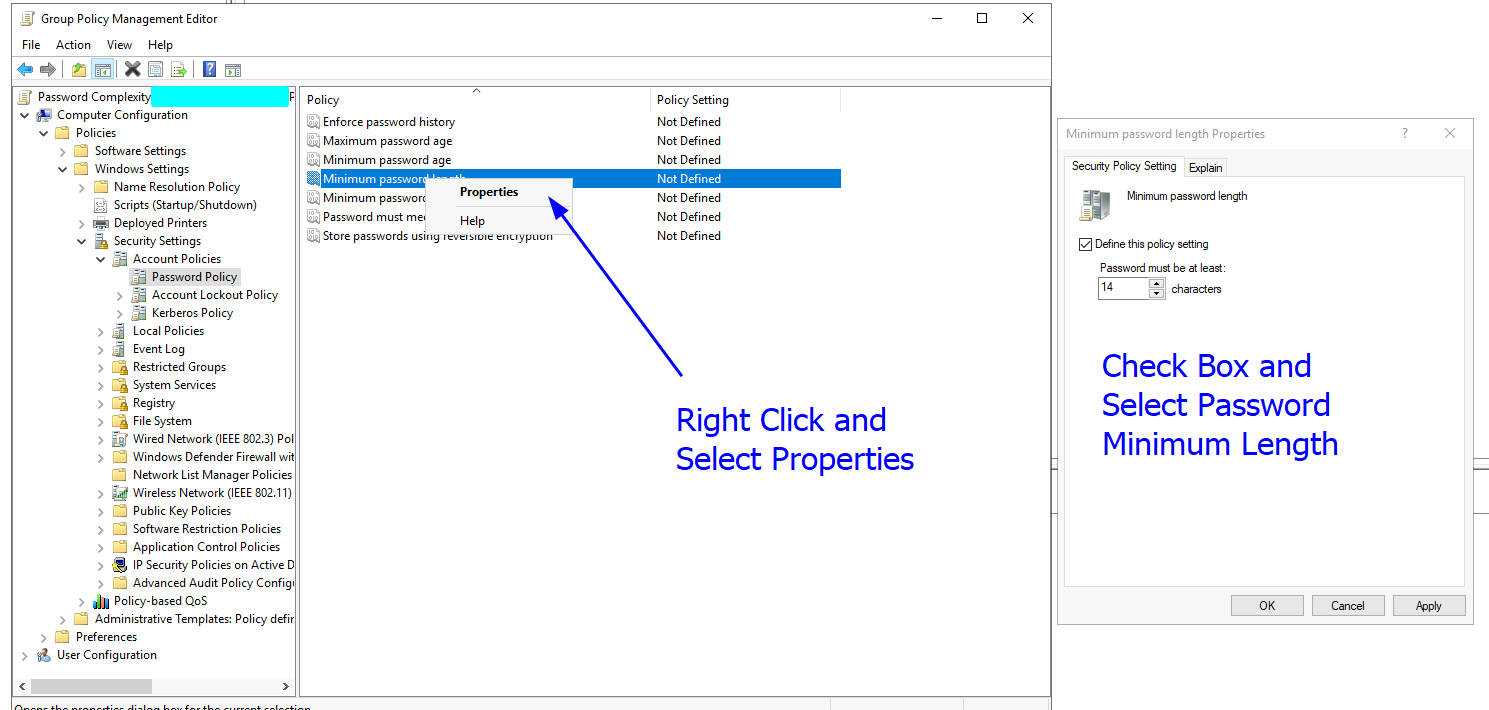
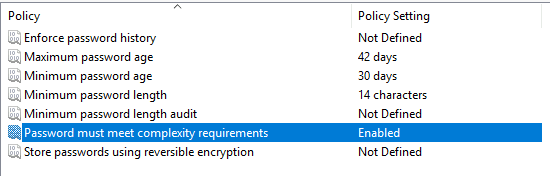
From here, a number of properties regarding password policy can be set including password minimum length, maximum age and complexity requirements. Right click each policy item and amend the properties. An example of a complete Password Policy GPO could look like the image below. Notice how password complexity has been enabled, and a maximum age for passwords has also been set
Once the GPO has been created, remember to link it to the relevant groups or even your entire domain/forest so the requirements are actually applied!