The Next Step in Your Security Journey: Vulnerability Assessments

Previously, we discussed the process of creating a Threat Map to identify ways in which attackers may target your organization and what you can do to begin mitigating those threats. The next step in your security journey is to conduct a Vulnerability Assessment. This process is an essential part of all organizations' overall risk management process. It allows you to identify where your organization is vulnerable, what vulnerabilities exist, and what steps you can take to reduce them.
What is a Vulnerability Assessment
A vulnerability assessment analyzes your IT infrastructure and applications to determine the security risks within your organization. For example, a vulnerability assessment can help you understand how secure your network is by identifying weaknesses in the way it's configured or used. Typically, a vulnerability assessment is a surface-level view of your environment to identify known vulnerabilities and misconfigurations but lacks additional information that helps to contextualize the overall impact that the risk presents.
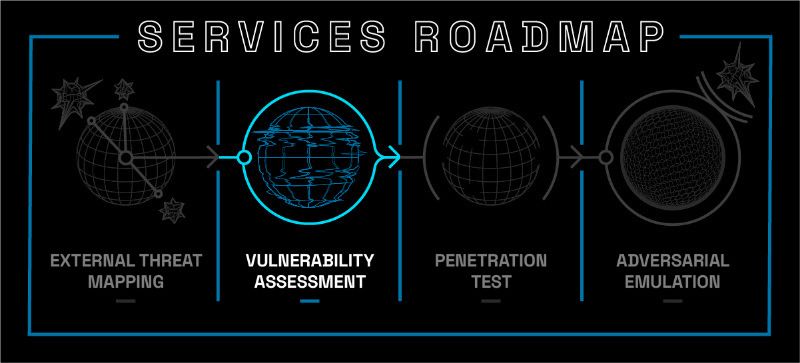
One thing to remember is that a vulnerability assessment differs from a penetration test (also known as a pentest). A pentest involves actively attacking systems to exploit vulnerabilities and determining whether exploiting a vulnerability might provide an opportunity to move laterally within a network or elevate permissions within the environment. A pentest may be conducted as part of a broader vulnerability assessment or separately as part of an overall security strategy--but either way, it will provide valuable information about where threats could arise so that you can plan accordingly. Pentesting will be discussed in the future, as it's the next step in the security journey after vulnerability assessments.
The vulnerabilities identified during an assessment vary depending on the environment being tested. For example, web applications may require different tests than networks since the environments and potential attack surfaces differ drastically.
What are the benefits of a Vulnerability Assessment?
Vulnerability assessments help you identify risks to your organization and prioritize security efforts, so you can stay compliant with regulations, avoid costly mistakes, and prevent data breaches.
A third party (such as us) can conduct vulnerability assessments internally or externally. The goal is to identify weaknesses in your systems that could be exploited by malicious actors if not addressed. This process will enable you to create actionable recommendations for improving the overall health of your IT infrastructure.
Conducting vulnerability assessments is the next step in proactive, preventative security.
Conducting vulnerability assessments is the next step in proactive, preventative security. It's also a necessary part of your overall security strategy. Vulnerability assessments can help identify and fix your security weaknesses before they become problematic.
Maltek Solutions has been working with businesses and organizations to help them conduct vulnerability assessments and penetration tests for years. We know this is an essential step in proactive security, which is why we are here to help you! If you want to learn more about a vulnerability assessment or how it can benefit your organization, contact us today.