How to Actually Disable Windows Defender
Article Purpose
People starting out on their computer security journey can be put off from using Microsoft Windows because the OS ships with a persistent antivirius (which is actually quite robust). Disabling this AV is required to load any sort of unobfuscated hacking tools onto the OS, but simply "switching off" Windows Defender in the Windows Settings menu does not actually deactivate it. I like hacking on Windows, and I want to make sure everyone knows it's doable.
You can develop malware in a Windows environment! You can own your computer!
Obligatory Introductory Rant
Microsoft gets a lot of hate for the Windows operating system, but I really don't think they are given enough credit for what they have built. Microsoft is a happy medium between the Ba Sing Se that is MacOS and the synapse-shredding jungle of Arch Linux. Unlike the extreme ends of the UX spectrum, Microsoft has built an operating system that can effectively be applied to both highly technical and highly creative use cases. As a consequence of this, creative users will often critique Windows for not being intuitive and technical users will often critique Windows for being a walled garden. The truth is that you can exert control over Microsoft Windows to the point that you feel like you actually own your computer. Unfortunately, to keep less technical users safe from themselves, the skill ceiling required to complete tasks that would be trivial in Linux is much higher for comparable tasks in a Windows environment.
Obligatory Legal Disclaimer
Useful Content
If you want to develop malware or just use Metasploit on Windows, you need to disable Windows Defender. Now, you might think that Windows would trust its users and allow them to switch it off in their settings, similar to sudo ufw down. One interaction and it's over, right? If you check out security settings, you would certainly think that:
If you're reading this article, you know this doesn't work :( You can still turn all of these settings off, but it will not prevent your device from quarantining threats.
So what do we do? It depends on the specific flavor of Windows you're using.
Disabling Windows Defender on Windows Home
The easiest way to completely disable defender is by using the Group Policy Editor, but Windows Home doesn't have that so we have to go straight to the registry:
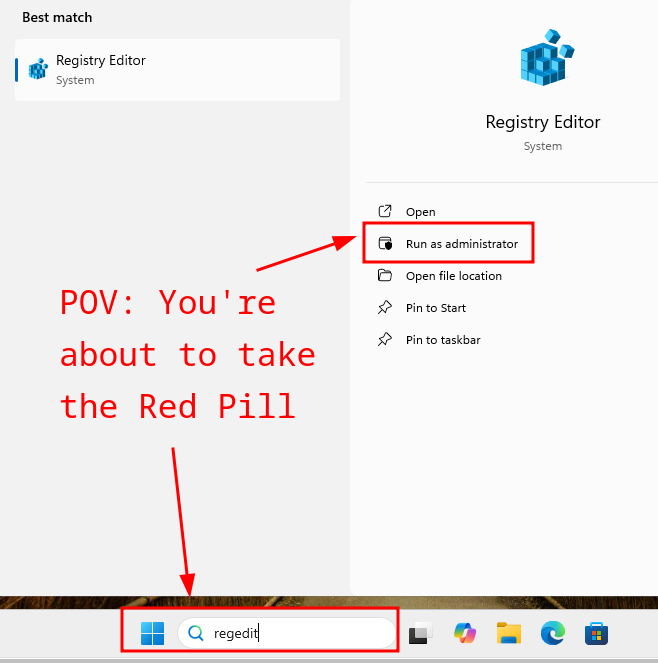
Once you get into the registry editor, there's a huge line of succession you have to chase down to get to the right location. And no, it's not in Security! Make a new DWORD value inside SOFTWARE\Policies\Microsoft\Windows Defender:
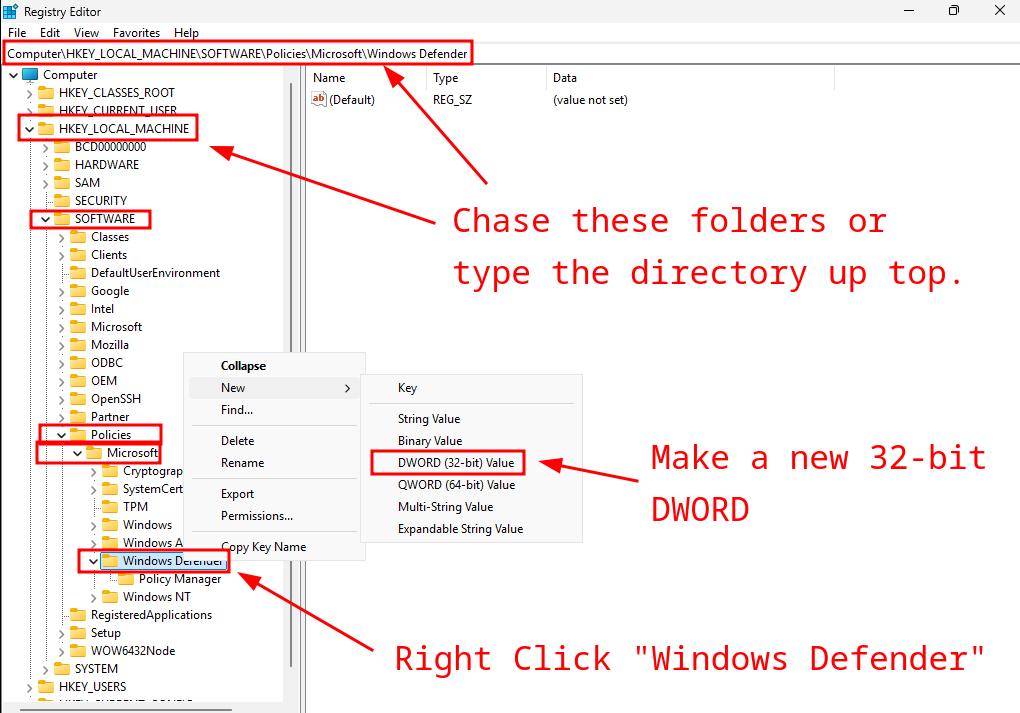
The new DWORD should be named DisableAntiSpyware. Once it's created, double-click the new entry and change the value to 1:
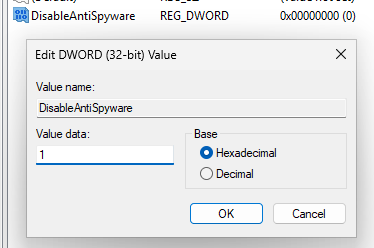
Restart the computer and Windows Defender should be inactive.
Disabling Windows Defender on Windows Pro/Enterprise
With Windows Pro, the user can edit Group Policy Objects, which makes the process of disabling AV a little less risky. Opening gpedit.msc will open a GUI window similar to the registry editor:
Navigating to Computer Configuration > Administrative Templates > Windows Components > Microsoft Defender Antivirus should show a policy object titled Turn off Microsoft Defender Antivirus, similar to the image below:
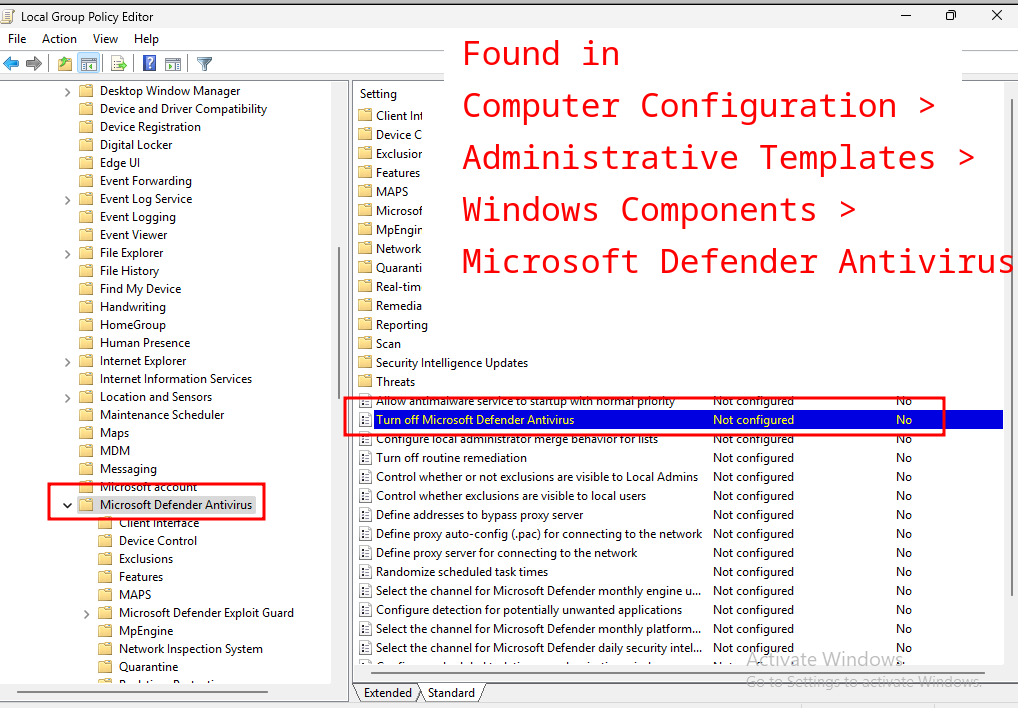
If you double-click this Policy Object, you can switch the value from Not Configured to Enabled which will turn on the policy that turns off Windows Defender:
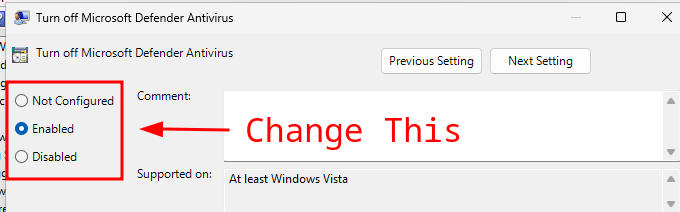
Restart your computer and Windows Defender should be deactivated for good. To prevent it from reactivating itself, make sure your Tamper Protection is also turned off in the regular Security Settings.
Obligatory Concluding Rant
I like Windows unironically. I started using it as my native OS because of Microsoft's corporate hegemony but soon discovered incontrovertible evidence of Windows' superiority in the dendritic pearl of Stockholm syndrome formed around my choice of OS. You can make Windows do what you want, it's just not as easy as Linux. I also firmly believe that if you are attacking Windows systems, you should be doing it from a Windows box. Since most targets in this field are Windows devices, you should know how to operate Windows machines with a prowess achievable solely from the practice of driving it daily. Microsoft maintains some of the best documentation I have ever seen, and this leaves no excuse for every network pentester or Windows malware developer not to have intimate knowledge of the Windows attack surface.
Begrudgingly Obligatory CTA
Marketing told me that I have to put a CTA at the end of every blog post so if you want a pentest click here.