Begin Your Security Journey: External Threat Mapping

While businesses are ever more connected to the outside world, they also face an increasing threat of cyberattacks. At the same time, IT security teams are under pressure to provide better protection while spending less on it. To meet these challenges, companies must move beyond perimeter-based security and look at all external threats across the extended enterprise. External Threat Mapping is a new approach that helps organizations identify and prioritize risks before they become full-blown attacks.
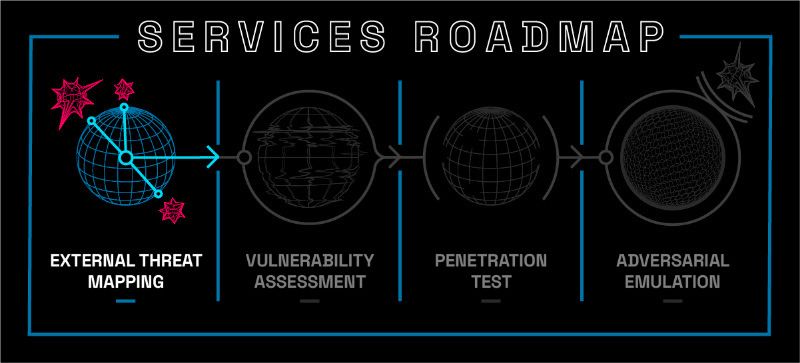
What is External Threat Mapping?
External threat mapping is a way to identify potential threats to your organization. A threat can be physical, like someone breaking into your building, or digital, such as hackers gaining access to your network. Threats can also be human or automated, intentional or unintentional, malicious or accidental.
Threats come in all shapes and sizes--and security teams need to understand them from every angle before trying to mitigate them.
You can use External Threat Mapping to understand better where your business is vulnerable to outside attacks.
External threats are those that come from outside your organization. They can be malicious software (malware), phishing scams, and other types of cyberattacks. External threat mapping can help you understand where your business is vulnerable to outside attacks, enabling you to create a plan for dealing with these threats.
Mapping also involves identifying all the external entities that interact with your company--including suppliers, partners, and customers--and then mapping out how they connect to your internal processes. Mapping can reveal weak spots in security measures and points at which data may flow out of the network without being protected by encryption or other safeguards against theft or unauthorized access by third parties who could use it illegally against your company's interests.
How Can Maltek Solutions Help
Maltek Solutions can help you map out your external threats. We'll work with you to understand the risks of your business and create a plan to mitigate those risks.
Once we've mapped out all of your external threats, we'll be able to identify areas where they might be coming from, such as:
- Hackers who are looking for ways into your system or network
- People who have access to sensitive data (like customer information)
- Third-party vendors that may not have adequate security protocols in place, allowing them access to sensitive systems or networks
Once we've identified these threats, you can take actionable steps to mitigate them.
Security is a journey, not a destination. It's important to remember that you can always continue improving your security posture and staying ahead of the bad guys. But by starting with threat mapping, you can understand how attackers might target your organization and find ways to defend against them before they strike.